Security configuration management software and change control software from Netwrix helps you secure critical IT systems and prove compliance
As industry regulations expand in scope and complexity, organizations need solutions that simplify the process of securing, monitoring and validating the configuration of critical systems. A strong compliance posture starts with secure systems configurations coupled with intuitive detection of unauthorized changes. With security configuration management and change control software from Netwrix, you can significantly reduce your organizations attack surface, detect & remediate breaches and pass compliance audits more easily.
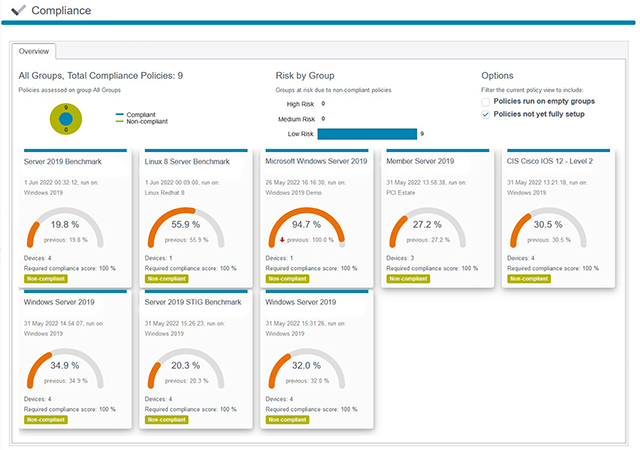
Ensure the integrity of your entire infrastructure from a single console
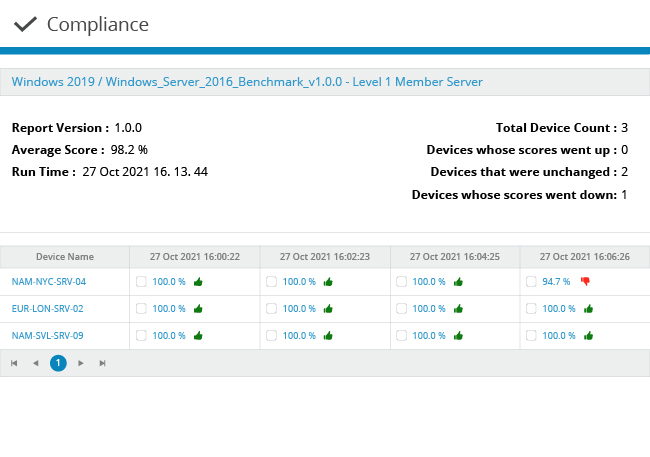
The Netwrix solution monitors your infrastructure from the cloud to the data center, across desktops, network devices and industrial control systems, giving you confidence that your IT systems and sensitive information are secure and compliant.
Learn how Netwrix advanced file integrity monitoring technology can help you protect your most critical systems
Netwrix Change Tracker protects all aspects of your infrastructure
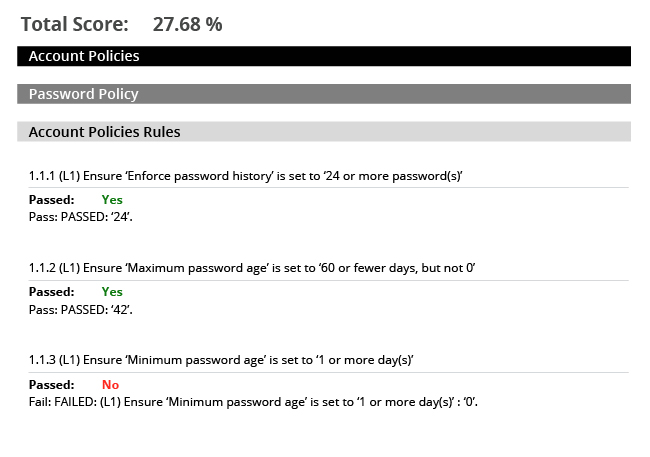
Harden the security configuration of your critical information systems
Find out how Netwrix helps you achieve
success with regulatory compliance
Navigating industry regulations can be difficult and time consuming without the right tools.
Netwrix offers a suite of solutions that address various aspects of regulatory compliance, enabling our customers
to succeed in implemeting the required security practices and to prove compliance.
Some of the regulations we support include:
Expand Protection With Product Add-ons
Newrix Change Tracker offers incredible features out-of-the-box and can be expanded to cover your specific needs with easy to deploy add-ons.
IT Service Management integration
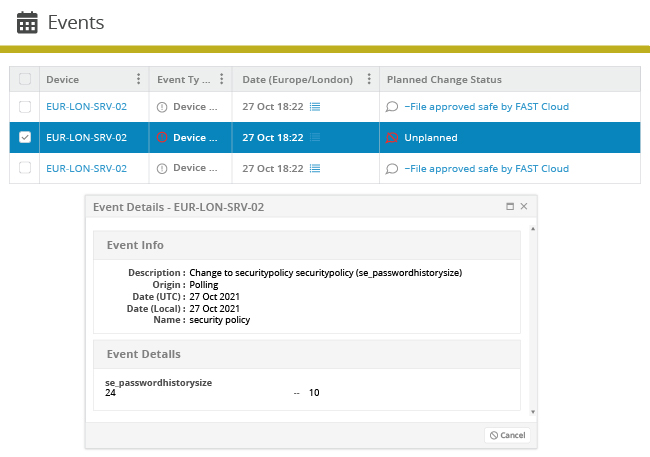
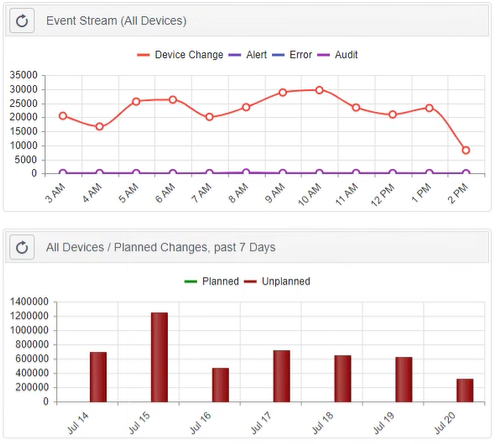
Connecting existing ITSM technologies with Netwrix Change Tracker to correlate the changes that occur within the IT environment with those that were actually planned and approved.
Service Manager
ChangeGear
Service Management
Service Management
Service Platform
Explore how Netwrix Change Tracker is empowering organizations like yours to harden their systems, improve security response and prove compliance