File Integrity Monitoring Articles
Read articles from industry experts New Net Technologies to find out about best practices in keeping your IT systems secure.
The ways in which File Integrity Monitoring can strengthen your security are threefold – through system hardening, malware protection, and change management. Click on a link below to find out more about how firewalls, servers, databases, servers and anti-virus programs can protect your IT systems.
Lots of coverage this week relating to ‘Hand of Thief’, the latest black-market Trojan designed for any aspiring cyber-fraudster – yours for just $2000. It’s concerning news in that the threat to your personal data – predominantly your internet banking details – is an increasingly marketable commodity, but for the IT community, the additional interest in this particular piece of malware is that it has been engineered specifically for Linux.
File Integrity Monitoring Software
Detect cyberattacks in their early stages with advanced file
and system integrity monitoring with NNT Change Tracker
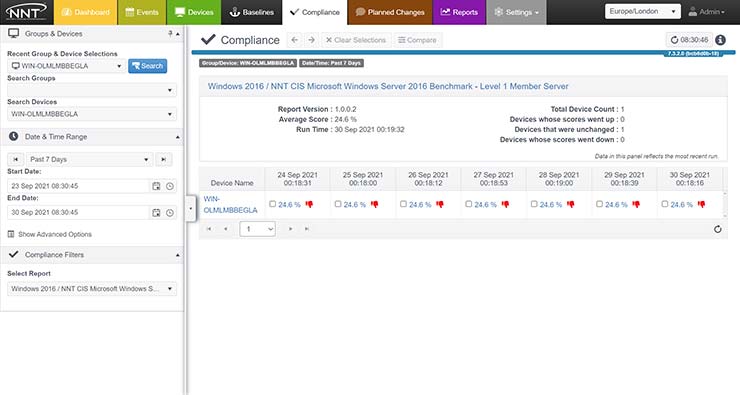
The longer an attacker can lurk undetected in your IT environment, the more damage they can do. But today, organizations need an average of 287 days — nine and a half months! — to identify and contain a data breach.
File integrity monitoring (FIM) solutions can help reduce the risk. Unlike traditional FIM solutions that focus on monitoring file activity, our file integrity monitoring solution is able to recognize known, expected and harmless file activity patterns, and detect and alert you on potentially dangerous and disruptive ones.
the NNT System and File Integrity Monitoring Tool
Spot true threat patterns promptly
Get notified about system changes that could be a sign of zero-day, malware or other cyberattack in progress.
Change Tracker monitors application files (e.g., DLLs), configuration files, registries, installed software, running processes, services and more.
Be confident that critical files are authentic
Quickly and accurately determine whether a change was part of planned maintenance, matches an approved change manifest or is whitelisted.
Reduce your compliance burden
Meet the requirements of PCI DSS, HIPAA, FISMA, CIS and other standards that recommend implementing FIM processes like monitoring changes to system and configuration files, performing critical file comparisons at least weekly, and more.
Harden your configuration management processes
Ensure that all IT systems remain securely configured at all times with at-a-glance visibility into event streams, planned changes, device activity and more.
Are you ready to get started in securing your IT environment with
industry-approved foundational controls, intelligent change control and automation?
Why use FIM in the first place? For most people, the answer is ‘because my auditor/bank/security consultant said we had to!’ Security standards like the PCI DSS mandate a requirement for regular file integrity checks, including log file backups/archives, and this is the initial driver for most organizations to implement FIM.
No guns were used, no doors forced open, and no masks or disguises were used, but up to $500 Million has been stolen from businesses and individuals around the world. Reuters reported last week that one of the world's biggest ever cyber crime rings has just been shut down.
Agent versus Agentless is a perennial debate for any monitoring requirements and is something that has been written about previously. The summary of the previous assessment was that agent-based FIM is usually better due to the real-time detection of changes, negating the need for repeated full baseline operations, and due to the agent providing file hashing, even though there is an additional management overhead for the installation and maintenance of agent software.
Every time the headlines are full of the latest Cyber Crime or malware Scare story such as the Flame virus, the need to review the security standards employed by your organization takes on a new level of urgency.