The website of Smith & Wesson was targeted by digital skimmers last week as they planted malicious code designed to steal customer payment card information.
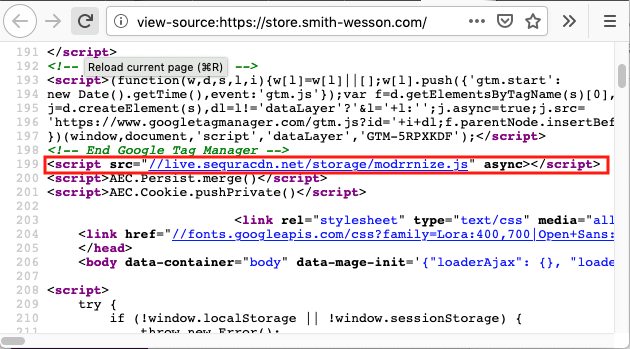
According to Sanguine Security, the attackers planted a payment skimmer on the Smith & Wesson online store on Wednesday, November 27, during the busy Black Friday holiday shopping weekend. The firm claims that as of Monday, December 2 that the skimming code is still active. The skimmer captures the personal and financial information entered by customers on the checkout page and sends the information to the attackers.
Strangely, the attackers have been using the Sanguine Security name as cover to legitimize the campaign. The security vendors forensic expert, Willem de Groot, claims, "Skimming code & infrastructure is identical to the campaign that impersonates Sanguine Security."
The attackers likely chose Sanguine Security deliberately, as much of their work is to protect customers from Magecart-style attacks.
This attack looks to be the work of one of the several hacker groups specializing in Magecart attacks, which require credit card skimmers to be planted on the online stores or through companies providing services to online shops.
It's suggested that the attackers exploited a known security vulnerability within the Magento eCommerce platform to hack the Smith & Wesson website. Magento recently warned its customers to install patches for a remote code execution vulnerability that can be exploited by unauthenticated users to deliver malware.
As of today, the malicious code is still present on the organization's website.
Macy's customers also recently had their payment details compromised due to Magecart code that compromised parts of their website.
To defend against this style of attack, organizations must implement security best practices and adopt the essential CIS Controls, which suggests implementing solutions like File Integrity Monitoring. Conducting FIM to detect and audit changes to key web application source code could be used to detect these kinds of breaches.












