Properly managing the configuration of your devices is vital for both security and regulatory compliance. This document explains what configuration compliance management is and how to achieve it.
What Is Configuration Compliance Management?
Configuration management for compliance means establishing and continuously maintaining proper configuration on all devices as required by regulatory mandates, industry benchmarks or internal policies. The process involves multiple efforts:
- Taking a thorough inventory of your servers, desktops, laptops and networking devices
- Ensuring all those systems are configured in line with applicable compliance standards and internal security policies
- Continuously monitoring those configurations for inappropriate or unwanted changes and mitigating configuration drift
- Creating reports for compliance audits
Netwrix Change Tracker can help with all these vital tasks.
Inventory of System Settings
Netwrix Change Tracker will collect all necessary data about the operating systems, installed applications and settings of your devices, and then help you define, maintain and prove a compliant state of those devices.
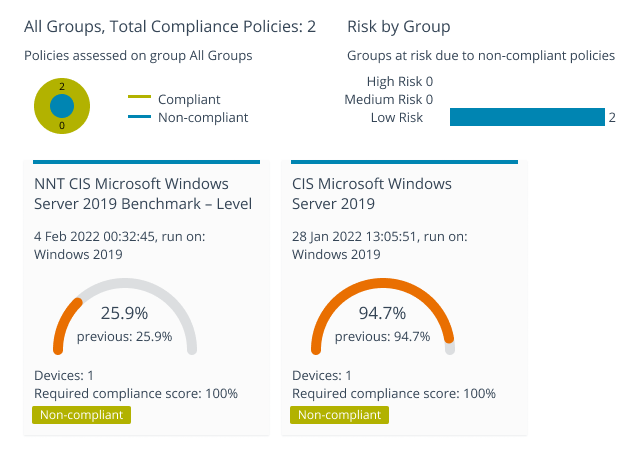
Device Management using Industry Standards, Benchmarks and Company Policies
Different organizations need different device configurations, based on the compliance mandates and benchmarks applicable for their sector, as well as their own IT and security policies.
Netwrix Change Tracker makes it easy to track your compliance with common standards like NIST, DISA, SOX, PCI-DSS and ISO27001; benchmarks from the Center for Internet Security and security technical implementation guides (STIGs) from DISA; and your organization’s own policies regarding device settings, operating systems and software applications.
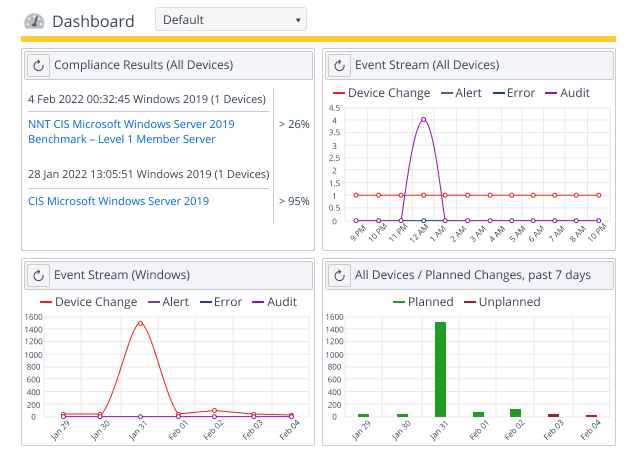
Continuous Monitoring for Improper Changes and Deviations
Netwrix Change Tracker will carefully monitor your infrastructure for changes and highlight modifications that are likely to be problematic because they deviate from known good settings or pose a security risk. It provides the full context for each change, including what changed, who made the change, whether it was planned, and whether it is likely to compromise your security and compliance posture.
Streamlined Compliance Reporting
Reduce the effort needed to prove compliance by automating repetitive tasks using over 250 reports covering CIS, NIST, PCI DSS, CMMC, STIG and NERC CIP.
