Compliance Audit Solutions that Satisfy Auditors and Secure the Enterprise
Quickly build and enforce a mature compliance strategy
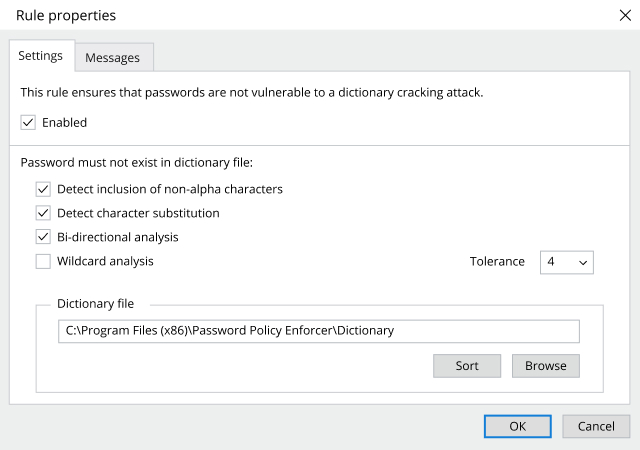
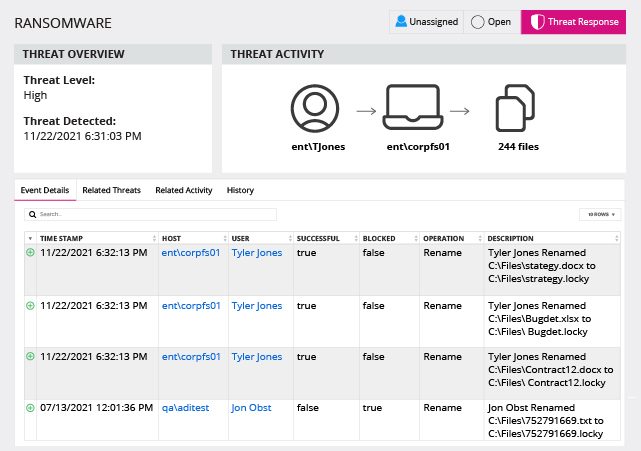
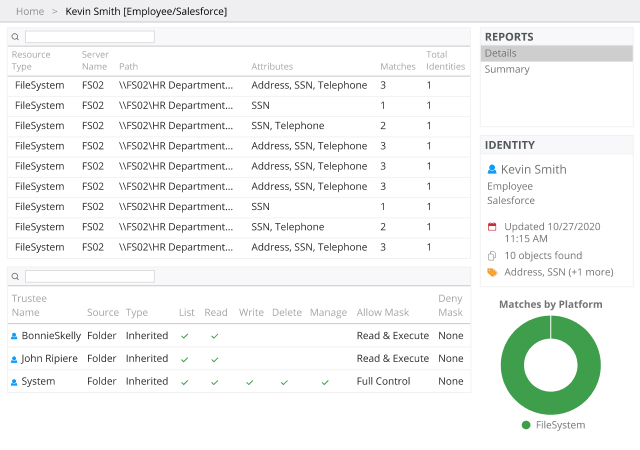
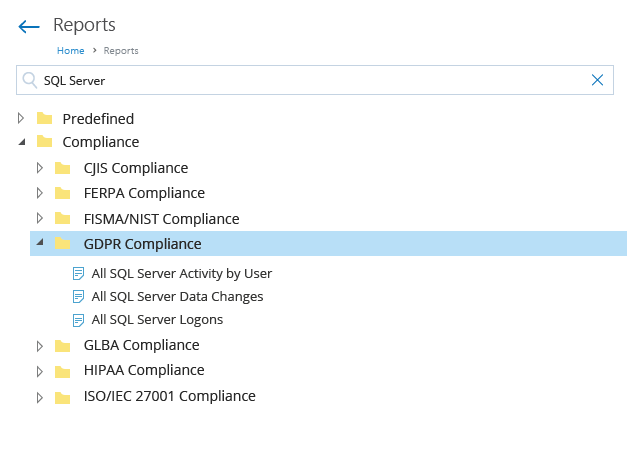
The Netwrix compliance audit solution empowers you to jump-start your compliance program with out-of-the-box templates, hardened build standards, password policies and more. Then it helps you continue to meet compliance requirements with features that enable you to maintain strong governance; quickly spot and shut down threats, meet incident reporting deadlines, and respond promptly to DSARs to avoid stiff penalties for non-compliance.
Slash preparation time for audits by up to 85%
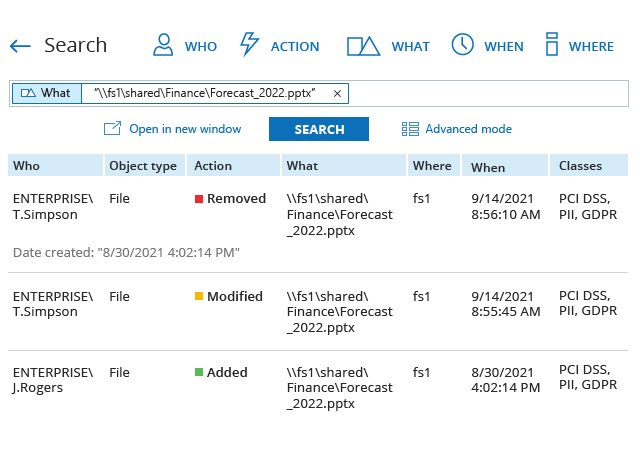
Reclaim the nights and weekends you used to spend collating cryptic logs, juggling spreadsheets and manually compiling reports for each external or internal audit. With the Netwrix compliance audit solution, you can prepare the evidence auditors require in just a few clicks, and answer any ad‑hoc questions on the spot during audit checks or inspections.
Maximize the return on your investments
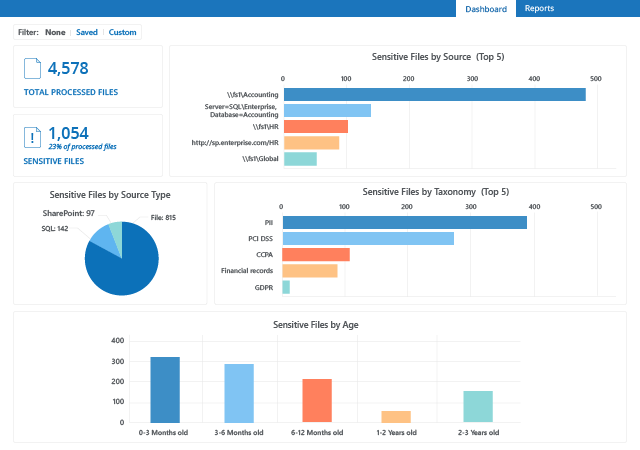
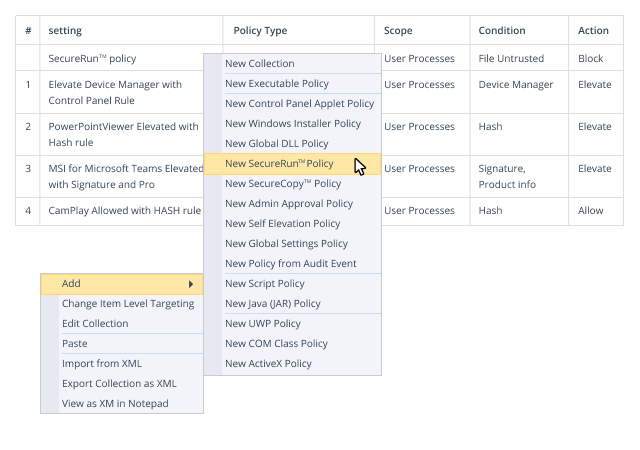
Invest once and get software solutions that not only satisfy compliance requirements but also deliver a mature, multi-layered approach to security; automate workflows to relieve the burden on IT teams; and empower your business to thrive by minimizing downtime, streamlining business processes, and enhancing user productivity.


.png)
_1664470399.png)