Unexpected changes to your system files at any time can indicate a network security breach, malware infection or other malicious activity that puts your business at risk. File integrity monitoring (FIM) helps you verify that system files have not been changed or that the changes are legitimate and intended.
Information security teams can improve their intrusion detection by adopting a solid FIM software solution that enables them to continuously monitor system folders on their Windows servers. Indeed, because FIM is so critical for data security, most common compliance regulations and security frameworks, including PCI DSS, HIPAA, FISMA and NIST, recommend implementing it whenever possible. Any organization that deals with highly sensitive data, such as cardholder information or medical records, is responsible for the protection and integrity of the servers where this data resides. For example, PCI DSS mandates deploying FIM to alert personnel about suspicious modifications to system files and performing baseline benchmarks at least weekly.
Although there are several native tools to check system integrity, they suffer from lack of critical features like real-time monitoring, centralized storage of security events, and context and clarity about why system files changed. These shortcomings make it nearly impossible for IT specialists to cut through the noise and understand whether changes are acceptable or potentially harmful. For these reasons, organizations with complex IT environments need to invest in reliable, context-based, Windows file integrity monitoring software.
Detect indications of data breach and malware infection in a timely manner
Netwrix Change Tracker audits system directory and file changes across Windows servers, tracking system updates installation and Windows registry changes. The application monitors the integrity of system files and configurations by comparing file hashes, registry values, permission changes, software versions and even configuration file contents. In case of any discrepancies, the solution will send easy-to-read real-time alerts indicating the abnormality that help users thwart malware activity and other threats in time to mitigate the impact. Detailed reports can also be generated at any time.
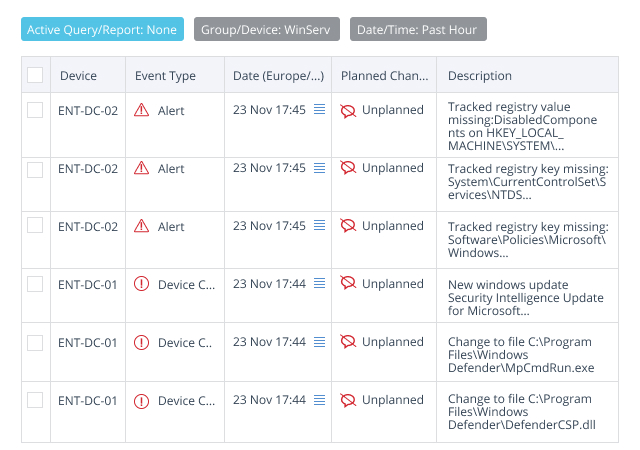
Take the guesswork out of file integrity monitoring
Netwrix Change Tracker is programmed to exclude planned changes and enable you to focus on the events that actually pose a threat. Moreover, its advanced threat detection is enhanced by the additional context provided by a cloud security database with over 10 billion file reputations submitted by original software vendors like Microsoft, Oracle and Adobe, helping to ensure highly accurate identification of improper changes.
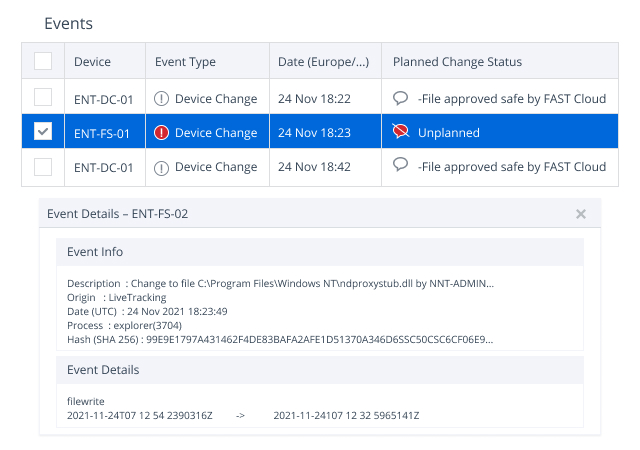
Reduce the time and effort you spend on compliance reporting
The software provides an overview of compliance scores for all Windows servers within any selected group. You can easily compare previous results to spot any drift from your security baselines and understand whether scores are improving or worsening. Netwrix Change Tracker is packed with wide range of pre-defined compliance reports, benchmarks and tracking templates, and reports can be exported in multiple formats to be provided to auditors or managers.
 (1)1658157537.jpg)
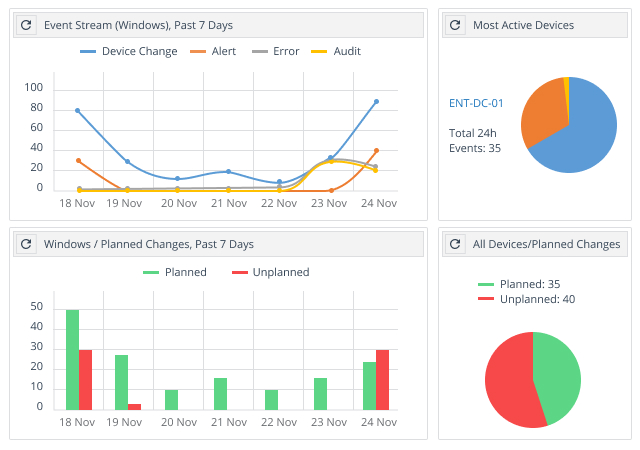
Get a bird’s-eye view of changes to the critical system files in your entire infrastructure
Netwrix Change Tracker provides a dashboard that shows recent system events, including:
- Planned and unplanned changes for a selected device group
- An overview of trends in compliance report results
- A summary of currently planned changes
- Potential problems with individual devices
With this actionable intelligence, you can quickly spot improper changes to configurations and critical files across multiple platforms, including Windows, Unix, Linux and MacOS systems, as well as network devices, virtualized systems and cloud platforms.