Configuration drift seems inevitable — the gradual but unintentional divergence of a system’s actual configuration settings from its secure baseline configuration. Proper configuration of your infrastructure components is vital for security, compliance and business continuity, but setting changes are often made without formal approval, proper testing and clear documentation.
This configuration drift in your systems and applications over time can create security gaps that put your organization at risk. Indeed, it is estimated that 1 in 8 breaches result from errors such as misconfigured cloud environments, and security misconfiguration ranks #5 on the OWASP list of the top 10 web application security risks. The more severe configuration drift, the higher the risk — but the reality is, even one misconfigured setting can expose an organization to data breaches and downtime.
This article explains some of the common causes of configuration drift and how to implement proper configuration management to reduce your risk of breaches, downtime and compliance penalties.
What causes configuration drift?
In most cases, configuration drift isn’t intentional. Its typically due to one of the following culprits:
- Software patches — While regular application of software and firmware patches is a best practice, it can result in unexpected changes to configuration items.
- Hardware upgrades — Hardware upgrades are also necessary, but they can lead to configuration changes at the hardware and software levels.
- Ad-hoc configuration and troubleshooting — Almost every IT team is guilty of sometimes applying a quick fix to address a workload or network disruption so that business operations can return to normal. While quick fixes may solve the problem at hand, they can involve configuration changes that hurt security in the long run.
- Poor communication in IT — Configuration drift can occur because one IT team does not inform other teams about a setting modification it made, or a new team member doesn’t know what configuration states are approved.
- Poor documentation — If configuration changes are not properly documented, team members may not be able to determine whether systems are properly configured.
The configuration drift resulting from these factors can result in poor performance or downtime, compliance issues, or a full-blown data breach.
Tips for avoiding configuration drift
NIST Special Publication 800-128 offers guidance for avoiding configuration drift. Here are some of the key recommendations:
- Implement continuous monitoring of configuration changes so that improper modifications can be identified immediately. Monitoring efforts should be supplemented by regular audits.
- Implement configuration tools that automate the creation, modification and deployment of configuration settings across your server and network infrastructure using established templates. Manual efforts are prone to human error, and slower than automated processes, so settings remain in a vulnerable state longer.
- Use a repository of benchmarks and baselines that IT teams can use to identify configuration drift. Consider using benchmarks from industry leaders like CIS or NIST as starting points to build your baseline configurations.
- Standardize your configuration change management processes to minimize the chance of configuration drift. Every configuration change should be approved and documented using this system.
Developing a secure baseline configuration for every IT endpoint
All of your desktops, servers, applications, network devices, containers and hypervisor platforms must be hardened with a secure configuration. By establishing a standard configuration for each type of endpoint, you can apply a consistent configuration across them. For example, by creating a standard configuration for your call center workstations, you can ensure they will share an identical operating system, patching level, software portfolio and Group Policy.
Baseline configurations will change over time, for example, due to software patches and operating system upgrades. Each change needs to be carefully reviewed for its potential impact on service delivery and security. Once an updated configuration is approved and authorized, it can be promoted to the baseline configuration, and all devices should then be audited according to the new standard. The NERC CIP standard such an audit every 30 days for all SCADA, human-machine interface (HMI) and programmable logic controller (PLC) systems required for energy production.
Automating Configuration Management with Netwrix Change Tracker
Looking for a way to establish secure baselines and implement strong change control to prevent configuration drift? Netwrix Change Tracker can help. It scans your network to find devices and makes it easy to create secure configurations for them using CIS-certified build templates. Then it monitors for any changes to these configurations and alerts you in real time about any unplanned modifications.
Establishing Your Baselines
Netwrix Change Tracker gives you access to 250+ CIS-certified benchmark reports that cover NIST, PCI DSS, CMMC, HIPAA, the CIS Controls and more. Using an intuitive wizard, you can fine-tune these benchmarks to meet your specific needs in minutes. You can easily create standard configurations for all your systems, from IoT systems like PLCs, relays and actuators to complex cloud and container infrastructure. Plus, any baseline image can be re-used to benchmark other systems.
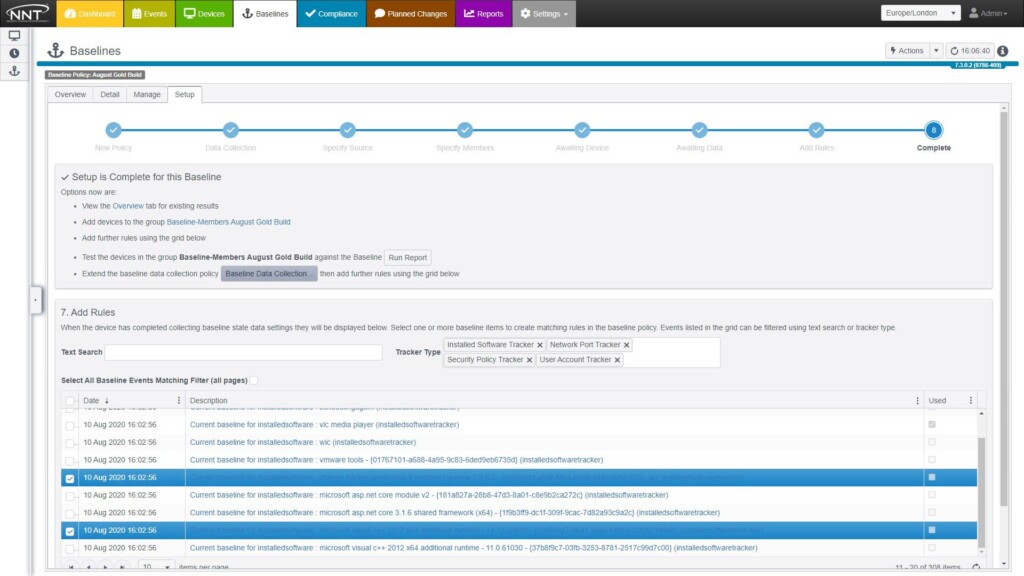
Maintaining Your Baselines
As noted earlier, your baselines will change over time. In particular, patches and updates can initiate changes to configuration, registry and port settings as well as the underlying file system. Netwrix Change Tracker puts you in charge of which settings get promoted to your baselines.
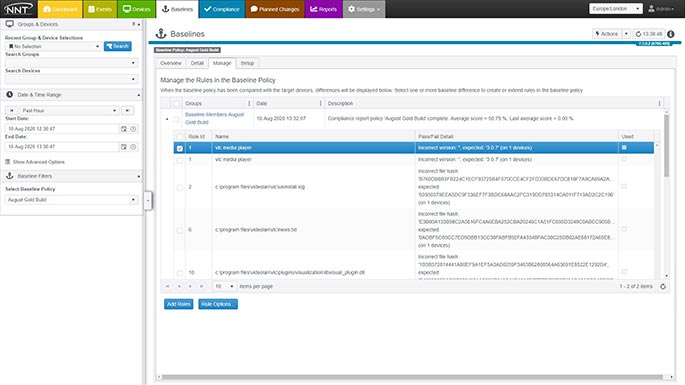
All build processes are anchored in security best practices. User permissions are controlled for all stages of baseline promotion, editing and creation. Plus, you get a detailed audit trail of the who, what, when and why details, so you can see exactly how any baseline image has been modified over time.
Spotting and Remediating Configuration Drift
Netwrix Change Tracker also provides advanced change control, using threat intelligence to pinpoint unwanted and potentially dangerous changes to system files. In fact, it uses billions of approved hashes to check new and altered file on your devices. That way, the massive changes from Microsoft’s Patch Tuesday will not flood you with alerts, but you’ll know right away about the malicious modification hiding in the haystack.
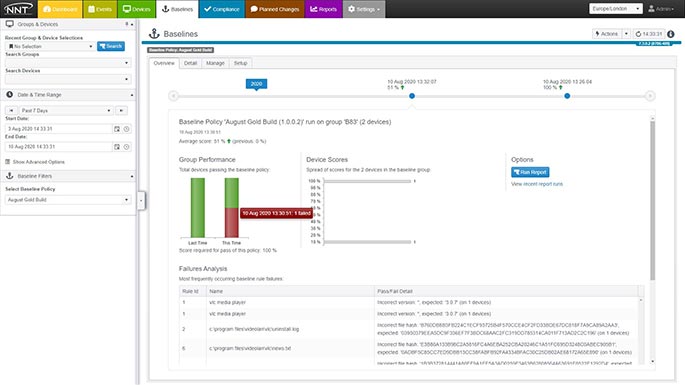
Conclusion
Change is inevitable, but you don’t have to allow your configuration settings to drift from their secure baseline. With an automated configuration management tool like Netwrix Change Tracker, you can establish and maintain secure configurations across your systems to avoid costly performance issues and downtime, security breaches, and compliance penalties.
FAQ
What is a secure baseline configuration?
A baseline configuration, or gold build, is the standard, approved configuration of a system. It can specify things like the approved operating system, patching levels and installed software. To make your baselines secure, consider building them based on CIS Benchmark or DoD STIG guidance.
How do I determine what the baseline configuration for my systems should be?
Establish a baseline configuration for each set of similar systems. For example, all workstations used in the accounting department should share the same baseline configuration.
Best practices for configuration hardening include the following:
- Uninstall any software that is not required, and remove all unused roles and features.
- Remove or disable any unnecessary services and daemons.
- Remove or block any unnecessary logical network ports.
- Keep all software patched to the latest levels.
However, keep in mind that you will likely need to balance security and business priorities as you create your baseline configurations. Where security has to give way to required functionality, you can compensate using other security controls, such as a web application firewall (WAF) or firewall services.
How often should a baseline configuration be updated?
Changes to your baseline configurations are inevitable and necessary. In particular, regular patching and updates are vital to defending against newly discovered vulnerabilities and gaining access to new software functionality. When these processes result in configuration changes, you should carefully assess their impact on service delivery and security, and then determine whether and how to update your baseline configuration. An updated baseline should be promptly applied to all relevant systems.
The NERC CIP standard requires auditing the baseline configurations of all SCADA, HMI and PLC systems required for energy production every 30 days.
What is a configuration management plan?
A configuration management plan defines a process for establishing baseline configurations, monitoring systems for configuration changes, remediating improper or authorized modifications, and maintaining baseline configurations over time.
How do I stop configuration drift?
Configuration drift is a common problem that can be managed with strong configuration management. In particular, you should:
- Establish a baseline configuration for each class of system and application.
- Plan all configuration changes, validate that they are enacted as planned, and document them.
- Monitor for changes to your configurations and triage them.
- Avoid applying ad-hoc or quick fixes to solve problems quickly.

