Ransomware Protection Software to Secure Your Data from Being Kidnapped
Reduce your attack surface by closing security gaps
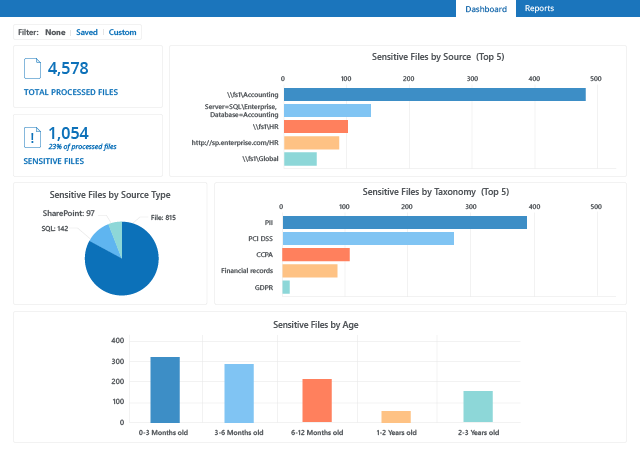
The latest types and versions of ransomware attacks are becoming extremely hard to notice by the naked eye, so even expert users may eventually get tricked. Although you can’t completely eliminate the risk of users opening malicious attachments or clicking the wrong links on the internet, but you can identify and mitigate weak spots in your security posture to minimize threats and potential damage — if you have the right anti-ransomware tools in place.
Keep calm knowing that you’ve done everything you could to prevent a ransomware infection
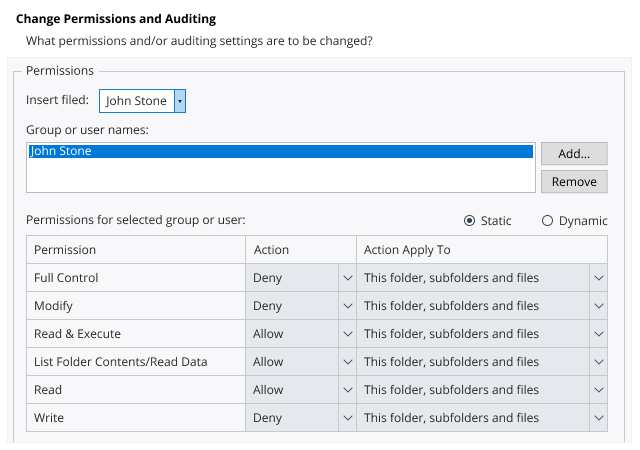
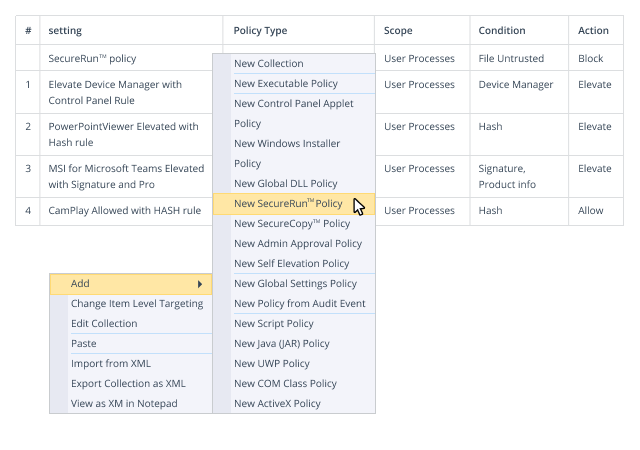
It’s said that an ounce of prevention is worth a pound of cure. Minimize the risk of ransomware breaking into your network by protecting your privileged accounts, rigorously enforcing least privilege and locking down Group Policy, so you never have to think of paying any ransom.
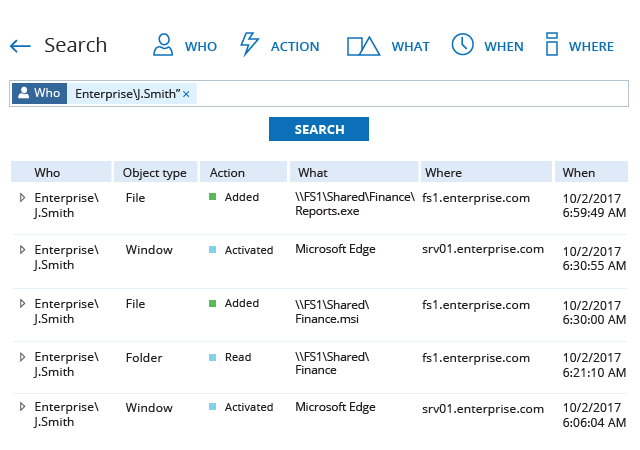
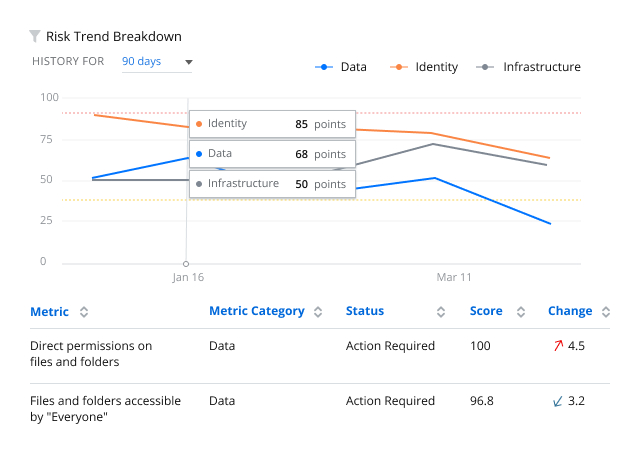
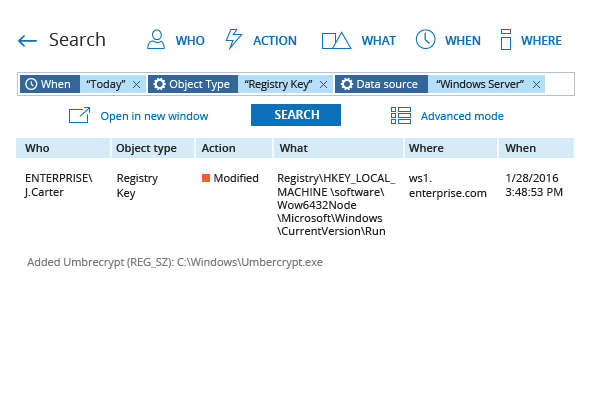
Discover ransomware in your environment in time to take action
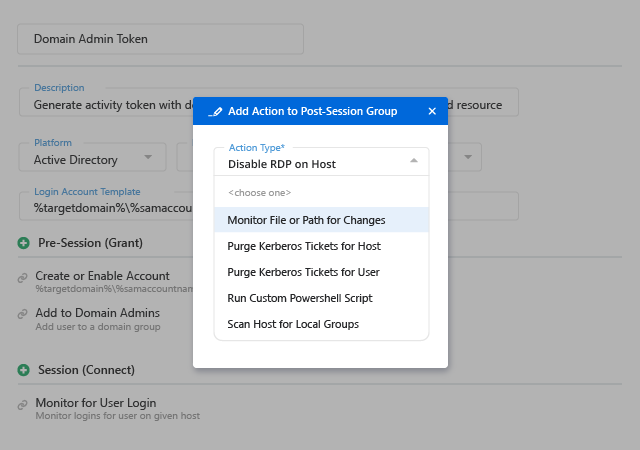
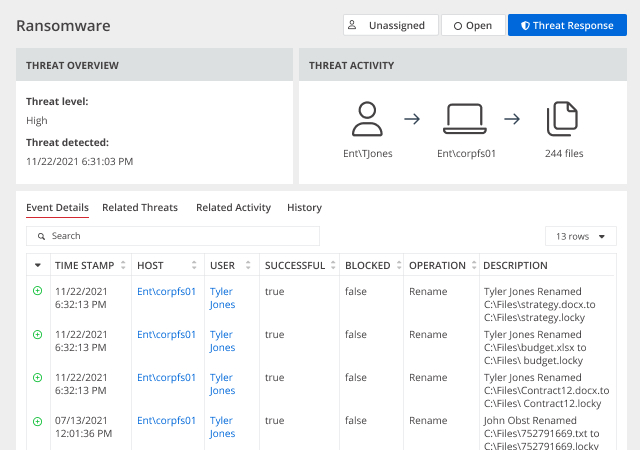
Follow an “assume breach” strategy — ensure that you can promptly detect ransomware that manages to get past your defenses and contain the damage to avoid costly business disruptions and compliance penalties. Netwrix solutions can help you spot and thwart a ransomware attack to keep your organization out of the news.
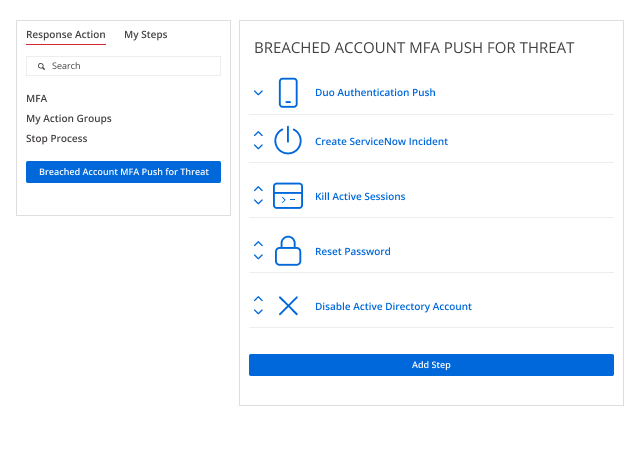
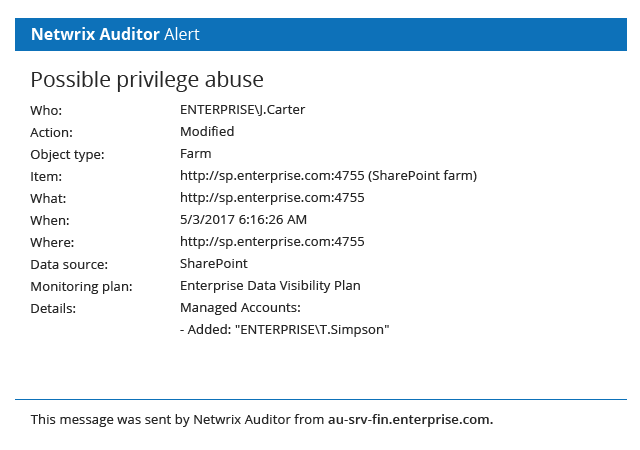
Stop ransomware in its tracks and minimize the damage
Some ransomware attacks are so catastrophic that the business never recovers. A speedy response is essential to minimizing the damage. Reduce the mean time to respond to attacks, minimize business downtime and facilitate quick recovery of key data.
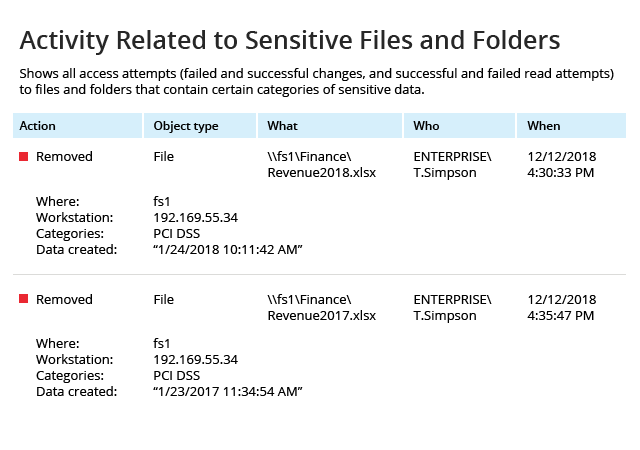
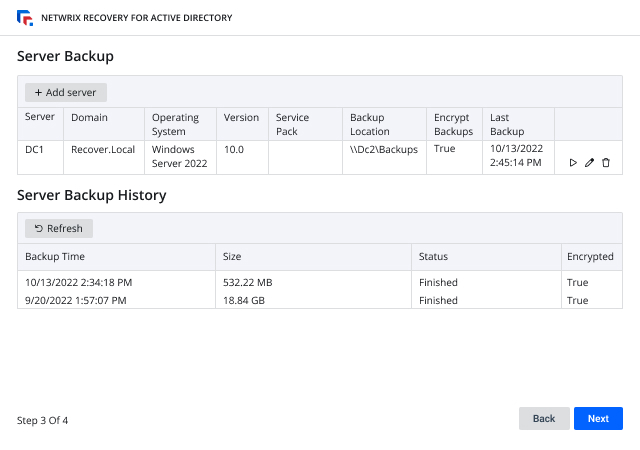
Minimize business downtime and get back to normal with less pain
Recover from ransomware incidents faster with detailed information about the attack. Revert quickly to a known-secure state and incorporate lessons learned into your data security strategy.
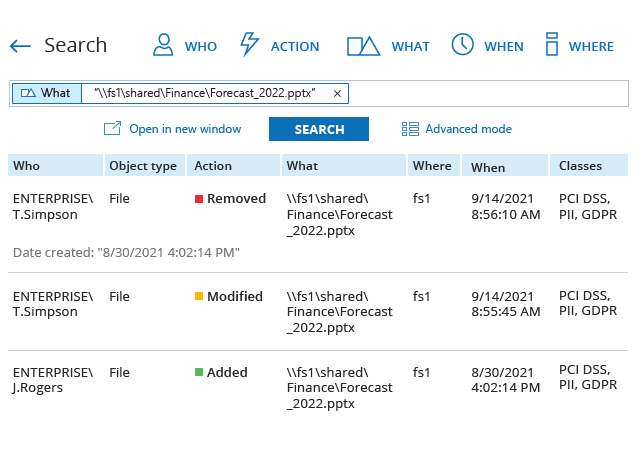
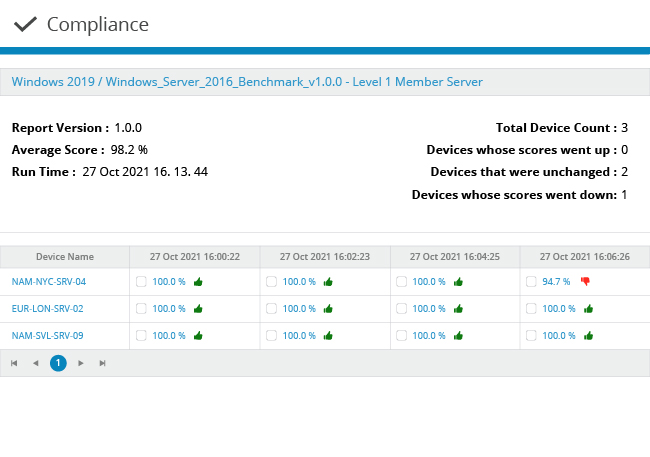
Ensure business continuity
Ensure that your IT investments support your business and security needs. Minimize the likelihood of Ransomware attacks and their potential impact on business continuity.



.png)
.png)
_1648636602.jpg)
.png)