Pokémon Go, the new GPS-based augmented reality OS and Android mobile gaming app, has been causing a riff amongst the cyber community, leaving many concerned about the privacy risks and cyber threats associated with this new application.
Researchers at Proofpoint spotted malware in a malicious Android version of the app that was downloaded by users in the US, Australia, and New Zealand from outside the Google Play app store, leaving many to believe the app was targeting users who were ‘sideloading’ the app before it was released in their region.
The infected version of the app was found to be infected with the DroidJack Trojan, allowing an attacker full control over a victim's phone.
“DroidJack gives attackers complete access to mobile devices including user text messaging, GPS data, phone calls, camera- and any business network resources they access,” said VP of Threat Operations at Proofpoint, Kevin Epstein.
But what seems to pose the most controversy are the privacy issues associated with the game. Game developers claim the app requests more permissions than necessary, in particular, their access to the user's Google accounts. It’s been noted that the app requires full Gmail account access, meaning Pokémon Go and Nicantic has permission to read emails, send emails as the user, and access all Google drive content and more.
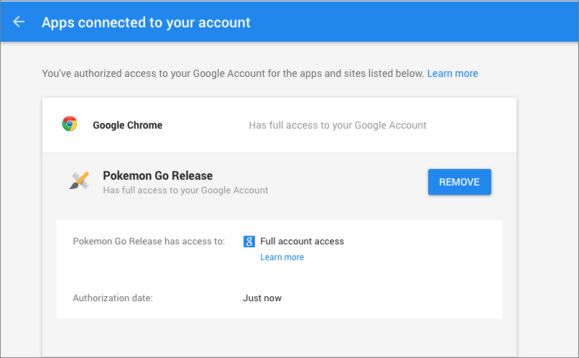
While the creator of the game, Nitantic, have since claimed it was unintentional and will be altered soon, this brings up an important dispute about app permissions and how much attention we really pay to them.
This poses not only personal privacy issues but also work related privacy issues. Who’s not to say someone who downloaded that malicious app used a work Gmail account to sign up, leaving a treasure trove of data open to criminals to abuse. Businesses need to remain vigilant in their fight to secure sensitive data and block access to any websites or applications that pose a threat to the organization.












