FIM Is Essential for Both Security and Compliance
File integrity monitoring (FIM) is the process of actively and continuously watching for changes in critical files. FIM is mandated by most compliance regulations and security frameworks for good reason: It is a critical security control that helps organizations both proactively block attacks and detect threats in their early stages.
While standard security defenses like anti-virus (AV) tools and firewalls are valuable, they do not provide sufficient protection against contemporary cyberattacks, such as phishing, ransomware, insider threats and Zero Day exploits. But FIM does. FIM works by monitoring changes in two types of files:
- System files — The binary program files that provide the core functionality for a device, platform or application
- Configuration files — Files that store the settings that govern the security and operational characteristics of a platform, device or application
As a result, FIM can help you achieve both of the following goals:
- Breach prevention: Organizations painstakingly harden their systems with the most secure configurations to maximize their resistance to attacks. FIM continuously watches for changes to configuration files that could introduce vulnerabilities that would enable attacks to succeed.
- Breach detection: Ransomware and other malware often cause changes in system files. By detecting those changes, FIM can spot cyberattacks in time to prevent serious damage.
However, effective FIM can be a challenge in today’s dynamic and heterogenous environments. You need a solution that:
- Covers your entire IT ecosystem, including all of your:
- Environments — On-premises systems; public, private and hybrid clouds; and dynamic container-based computing
- Platforms — Not just Windows, but RedHat, Ubuntu, and legacy Unix platforms like Solaris and AIX
- Appliances and devices — From firewalls and routers to the fast-growing array of IoT devices
- Makes it easy to establish secure gold-image configurations using sources such as CIS benchmarks and DISA STIGs, and to assess whether your systems match those baselines
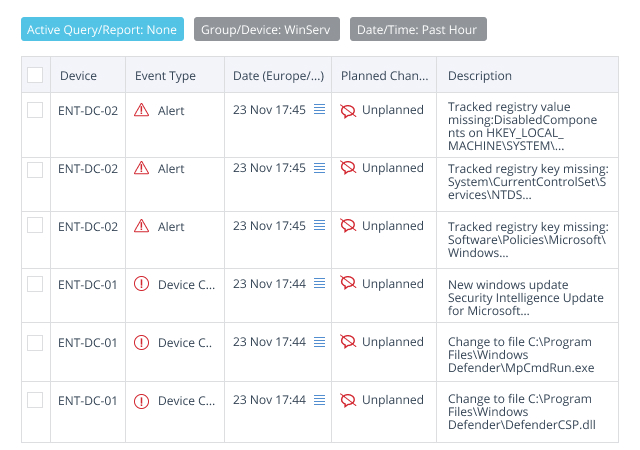
- Focuses attention on true threats by filtering out the noise of scheduled patching activities and other planned changes
- Alerts on unplanned, unexpected, suspicious changes, providing all the key details required to speed investigation and remediation
Why Choose Netwrix Change Tracker for FIM?
Not all FIM solutions deliver these key capabilities, but Netwrix Change Tracker does.
Get laser-focused on the changes that matter.
Most FIM solutions simply track file activity, which leads to two related problems: change noise and alert fatigue. The changes you really need to know about — unauthorized or improper changes that increase security risk — get buried in the noise from all the legitimate changes in the environment caused by processes like patching and normal system operations.
Netwrix Change Tracker, however, intelligently analyzes all changes in real time to exclude planned and expected changes. As a result, your teams can focus on the events that actually pose a threat, instead of wasting valuable time on false alarms.
Take the guesswork out of file integrity monitoring.
Netwrix Change Tracker uses a cloud security database with over 10 billion file reputations submitted by original software vendors like Microsoft, Oracle and Adobe. This context further helps ensure highly accurate identification of improper changes.
Reduce the time and effort you spend on compliance reporting.
With Netwrix Change Tracker, you can easily review the compliance scores for all your devices and see whether the scores are improving or worsening. Plus, the solution is packed with wide range of pre-defined compliance reports, benchmarks and tracking templates that help you achieve compliance — and prove it to auditors.
 (1)1658157221.jpg)
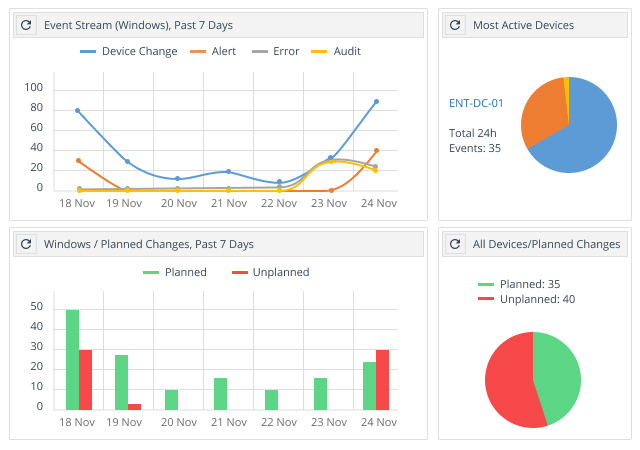
Get a bird’s-eye view of changes to critical system files across your entire infrastructure.
An easy-to-understand dashboard makes it a snap to spot improper changes to configurations and critical files across your Windows, Unix, Linux and MacOS systems, as well as your network devices, virtualized systems and cloud platforms. For example, you can quickly review:
- Planned and unplanned changes for a selected device group
- Trends in compliance report results
- A summary of currently planned changes
- Potential problems with individual devices
Key benefits
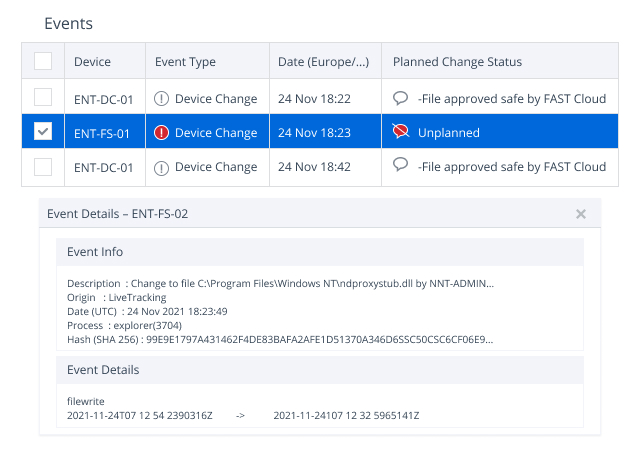
- Fast and accurate threat detection. Netwrix Change Tracker exposes threats, including Zero Day and Trojan file insertions, by tracking changes to all file attributes, contents and hash values. It also improves incident triage by capturing the vital who, what, when and how details for each change.
- No alert fatigue. Moreover, Netwrix Change Tracker slashes change noise with comprehensive threat intelligence, file whitelisting, exclusion of particular files and paths, and intelligent change control that learns to differentiate between planned changes and suspicious activity.
- Comprehensive system and device coverage. Be confident your organization is covered from the datacenter to the desktop, both on premises and in the cloud.
- Hardened build standards. Easily establish secure, standard configurations across your IT ecosystem. You can base your build standards on a framework like CIS or DISA STIG, create bespoke standards, or derive a gold-standard configuration from an existing system.
- Alerts on configuration drift. Netwrix Change Tracker monitors your systems for any changes from your standard configurations and notifies you immediately about any drift that could weaken your security posture.
- Improved incident prevention, triage and recovery. Streamline and strengthen vital security processes by easily integrating Netwrix Change Tracker with your SIEM, ITSM and other tools using its well-documented Rest API.
- Flexible deployment options. Choose the approach that works best for your unique requirements: on-premises, SaaS or fully dynamic container-based deployment.