System Hardening / Vulnerability Management – the science of rendering servers, database systems, firewalls, EPOS systems and all other IT devices fundamentally secure is still the most effective - but often the most neglected - security best practice.
Todays’ contemporary networked systems rely on inter-operation, ease of use and open access – all in direct opposition to system security. A Hardened System is one that has a ‘locked down’ configuration, removing all unnecessary function, access and other potential vulnerabilities that could be exploited by a hacker.
Here at NNT we are advocates of hardening and NNT Change Tracker is bursting at the seams with compliance hardening reports from the Center for Internet Security. Nevertheless, we are always looking for Change Tracker techniques to improve our customer’s security stance and a baseline of process is one such approach.
Gathering process information with the aim of building a baseline is not for the faint hearted! It requires time, patience (a lot of patience J ) and also a system or systems which closely represent your production environment. The procedure,however, is very straight forward and is no more complex than cycling through the following on a representative system:
- Enabling the NNT agent’s process discovery to build the initial baseline
- Analysing and accept the results
- Enable the NNT agent process alerting
- Run the system through its normal life cycle of tasks
- Analyse any process alerts and add into the baseline
- Continue to run system tasks
- Continue to analyse any process alerts and building them into the baseline
- Repeat until all likely processes have been captured by the baseline
To demonstrate, the below example runs through a cycle of this procedure to highlight how things could be done!
The initial step is a baseline of the running process and so in an effort to collect as many valid processes as possible, consider opening features on the system which may be used, for example, the service management page and task manager.
To begin gathering baseline data, either create a new or edit an existing Change Tracker template from Settings > Configuration Templates.
Move to the ‘Process and Services’ tab
Check ‘Track processes and services in this template’
Select ‘Show Advanced Processes Options’
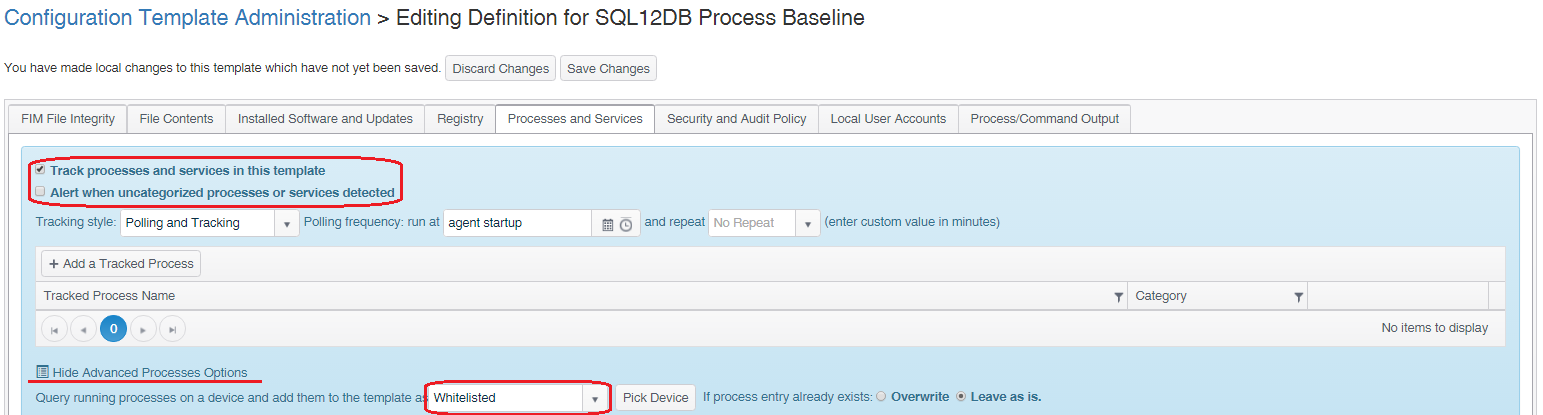
In the dropdown list select ‘Whitelisted’. There are a number of options here and whitelist is the most suitable for this task, nevertheless a description of all options is below.
Required: The Process/Service must be in the state required and an alert will be raised if this is not the case
Whitelisted: The Process/Service is allowed to be present but this is not mandatory
Blacklisted: The Process/Service is never allowed to be present and an alert will be raised if this is not the case
Graylisted: The process/service has not yet been allocated to another category
With Whitelisted added press the ‘Pick Device’ button and select the system from which the baseline will be taken.

The initial baseline will now be complete. Check ‘Alert when uncategorized processes or services detected’ and save the changes.
The template is now built so before we start the analysis process, a couple of key Change Tracker tasks!
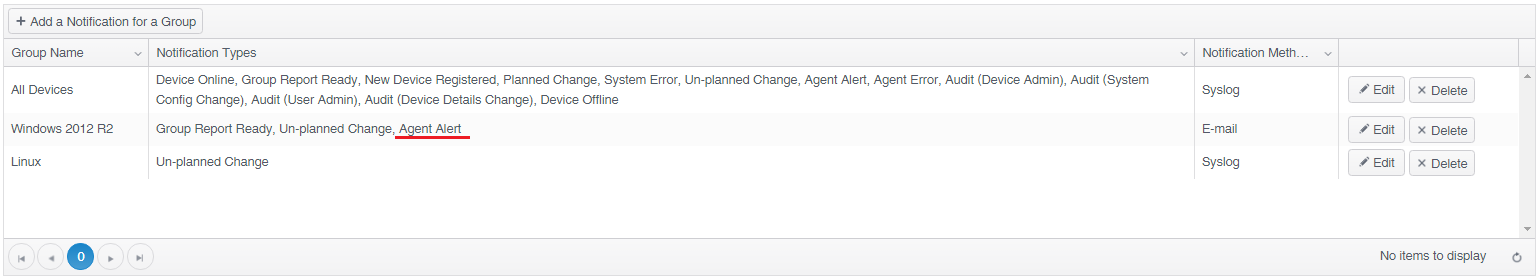
1 - If you have created a new template, link the template to a Change Tracker group and apply the group to your representative system from Settings > Agents & Devices.
2 - If you want to receive email notifications relating to unrecognised processes, set the ‘Agent Alert’ notification type in your profile ‘User Notifications’.
It’s now time to transition into monitoring. Allow the representative system to run through a normal lifecycle of operating system activity, application usage, system management and monitoring tasks. Any process which was not running during the initial baselining will result in an alert, termed within Change Tracker as ‘RuleViolation: Uncategorized process’. The alert will detail the process name, the port number the process is using, its executable path and also the associated account.
These alerts can be seen from the Change Tracker Event screen, where then can be exported for review and If enabled, via email notifications.
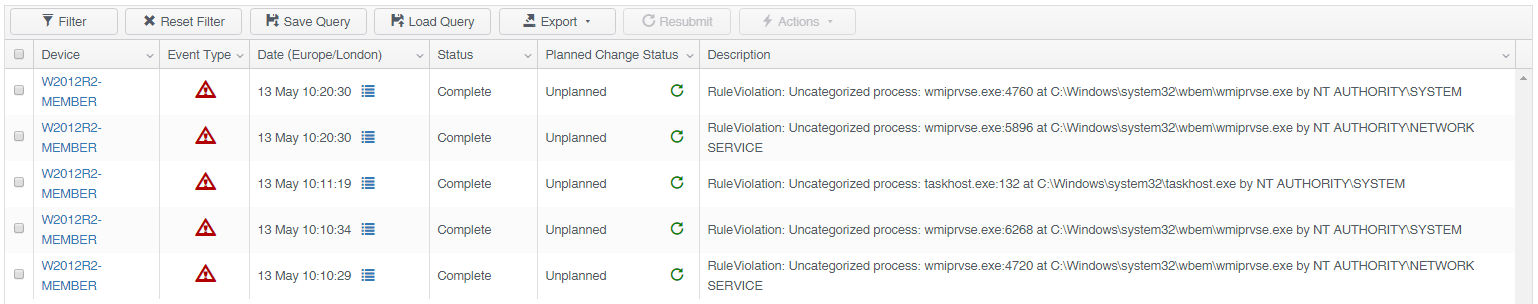
Figure 1 - Change Tracker Events
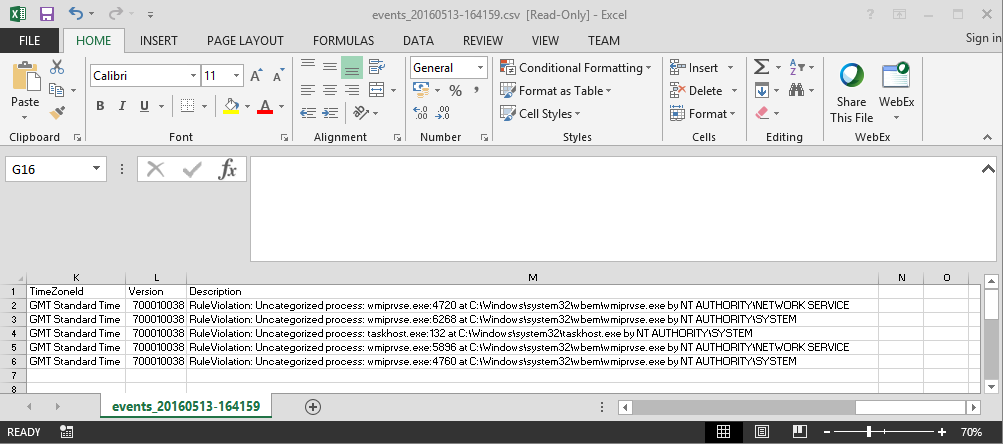
Figure 2 - Event export
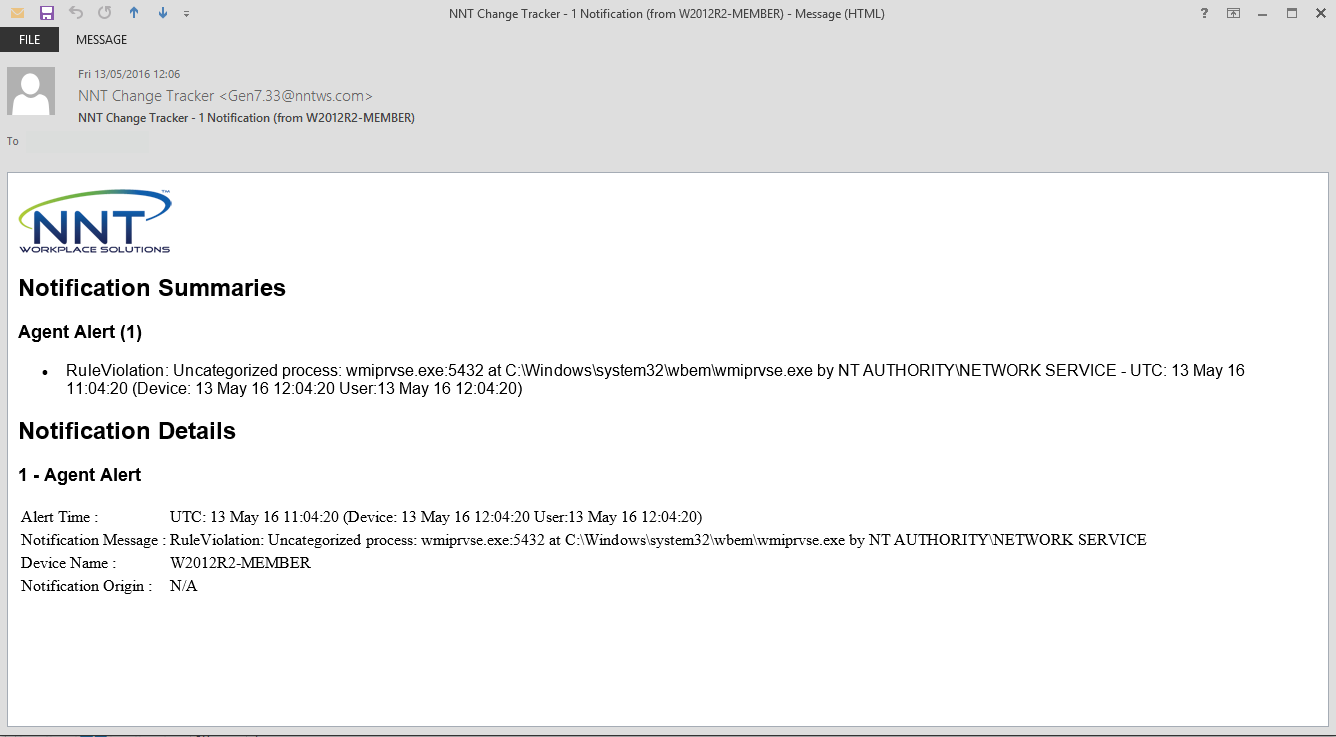
Figure 3 - Email notifications
It won’t take long for a number of processes to be gathered. In our monitoring example, the processes identified in the figures 1 to 3 are taskhost.exe and wmiprvse.exe. Taskhost is a native Windows process and Windows Management Instrumentation (WMI) is in use to monitor this system, so these processes are valid, deemed to be acceptable and can be added to the process baseline.
To add processes to the baseline, reopen the template, press ‘Add a Tracked Process’ and paste the executable into the field provided.

Once the processes have been added they will not appear as alert events again and we revert back to monitoring and collecting processes. If we keep repeating this cycle of reviewing detected processes and adding them to the baseline, it will not take long to build a comprehensive list of allowed processes.
Armed with this template, packed full of process knowledge, we can apply the baseline to our production environment. This will further extend our hardening stance and ensure that we will be alerted when new and unrecognised process appear on our systems.
As ever, hopefully the process described here has been useful and the description clear. If you have any further questions about process baselining or any other Change Tracker topic, please contact support!










