Webinar: Nightmare On Ransomware Street - Lock Your Digital Doors
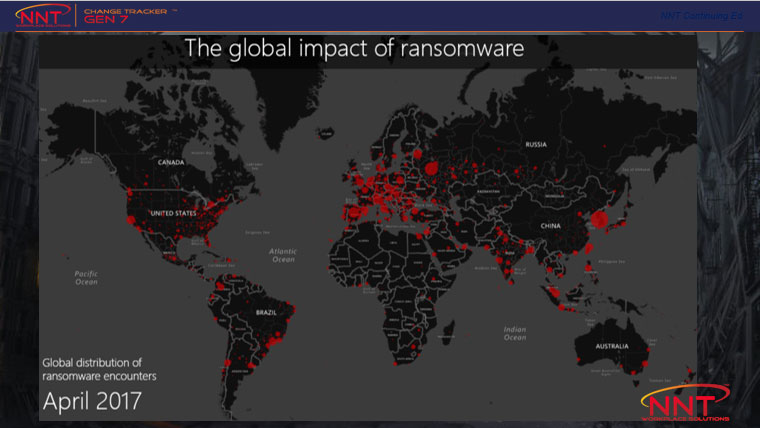
Halloween has been and gone: the time where we share scary stories knowing they’re confined to story books and movie screens, but unfortunately, there are some IT horror stories that are all too real: the scariest being ransomware.
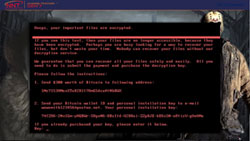
Unlike your typical Halloween monsters, these digital monsters, or hackers are real & use fear to get users to hand over cash or assets in exchange for decrypting essential and valuable files.
Under no circumstance should you give in to fear and pay the ransom demanded by a hacker. Instead, learn from our assembled team of experts what you can do right now to remove the main risks of infection and sleep better at night.

Listen to NNT CTO and CEO as they discuss:
- The Anatomy of a Ransomware Attack
- Proven Steps to Prevent a Ransomware Attack
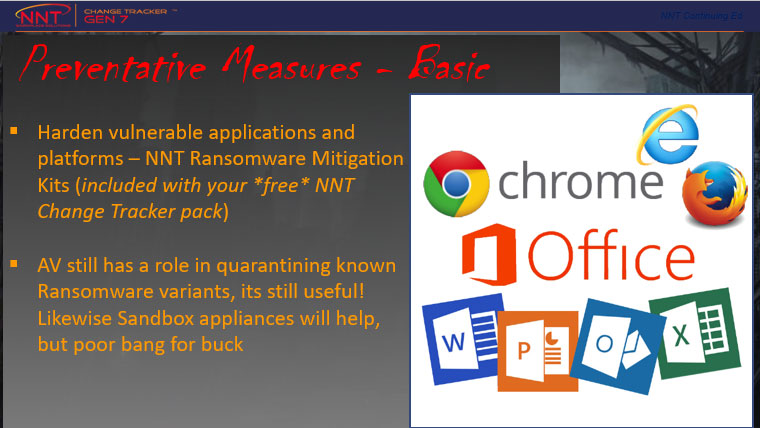
- Access to Ransomware Mitigation Kits
- Tools to help handle Ransomware fears throughout the organization
Video Transcript
Mark Kerrison
As the CEO at New Net Technologies, Mark works closely with all departments within the business to ensure NNT is optimized to continue to bring innovative cyber security solutions to market as well as ensuring that the correct support process exists to facilitate successful deployments and that ongoing solution value is maintained for all customers.
Mark Kedgley
As the CTO at New Net Technologies, Mark is the technical lead within the company and is responsible for researching the latest market trends, identifying the technological requirements and translating these points into innovative product functionality.
NNT
New Net Technologies is a global provider of data security and compliance solutions. Clients include NBC Universal, HP, RyanAir, Arvato and the US Army.
NNT Change Tracker Gen 7 audits your IT estate for compliance with best practices in security configuration, provides real-time, zero day malware protection and protects systems from any unauthorized changes: